Detect phishing in emails
Phishing is one of the most obvious threats at our university.
If you receive any suspicious emails, please delete them immediately. Above all, do not click on attachments or links. You will never be asked by the university to provide username and password. If you receive links from UNIGRAZonline, Moodle or other university systems, please always check if they correspond to the actual links.
Tip: Never give your university email address for private purposes.
Subject: Even the subject can be an indication of a phishing email. If the subject does not match the usual circumstances, then this is already a strong indication of a phishing email.
Example: If you do not have an account at a partner university and the subject is about this account "Your mailbox RWTH Aachen is full!", then it will probably be a phished email.
Sender: Sender addresses can be forged at will, just as with a postal letter! An e-mail is only falsifiable based on the sender address.
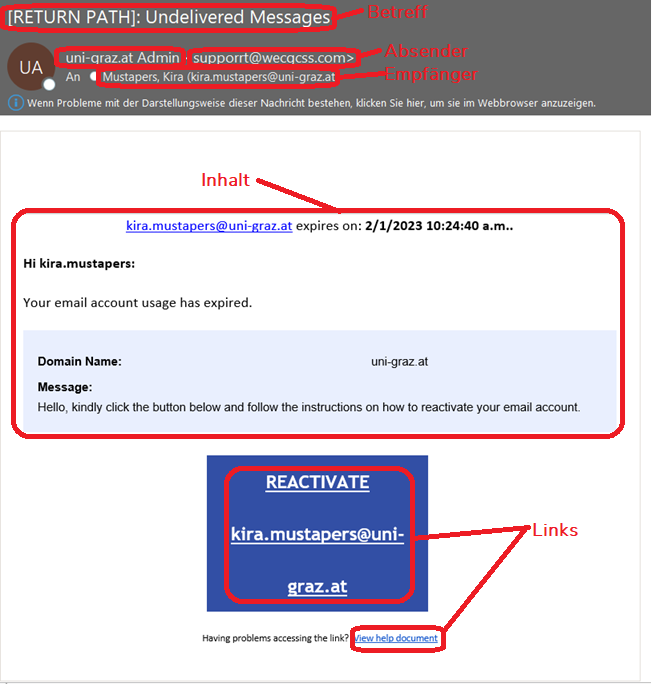
Example, see figure: Is the sender address unknown? If the subject and content of the e-mail [It is about an e-mail account of the University of Graz] do not match the sender domain or the sender address [supporrt@wecgcss.com, here one would expect uni-graz.at], the e-mail is most likely faked.
Recipient: The recipient address of an e-mail does not have to be your personal address or can even be empty! This is the case, for example, when sending to your e-mail address via Blind Carbon Copy (BCC). Attackers use this option primarily to confuse you or make you curious and thus tempt you to behave carelessly.
Email content: Here, several aspects can point to a forgery:
-
Language: is the email in a local language you would expect?
-
Spelling/grammar: Often phishing emails are translated (automatically) into the national language of the potential victims. Massive errors in spelling and grammar can be a clue.
-
Formatting: If an e-mail does not correspond at all to the (familiar) layout of a known organization (corporate identity), this can also be a clue.
-
Form of address: If, for example, the (supposed) sender addresses you by your first name in an e-mail, even though they are actually using the first name, this is also suspicious. If you are addressed by your e-mail address in a personal e-mail, this should also make you suspicious?
-
Context/characteristics: If the content of an e-mail does not match the (alleged) sender's usual way of expression, this is also suspicious.
References / links: Links in an e-mail can already be viewed in a pop-up window by moving the mouse pointer to them. On the cell phone by holding the finger on it for a longer time. If the links do not match the context, the page should not be opened at all. Unknown pages could be phishing pages (fake login pages that look like they are from Uni Graz, where you then enter your access data for the attackers, see example) or even contain malware.
Example: Links from the University of Graz can be recognized by the following characteristics:
online.uni-graz.at/irgend/was/kommt/noch.html.
meethi.in/blog/email.uni-graz.at.html is not a valid link of the University of Graz
File attachments: File attachments are a convenient way to exchange files. Not only from a security point of view you should exchange files in a different way. Better is e.g. the use of uniSHARE, uniCLOUD or SharePoint. If no IT services of the University of Graz can be used, you are on the safer side with personal data if you use exclusively European cloud providers.
File attachments from attackers often contain malware and the contents can also be disclosed to third parties in the case of unencrypted e-mail. The malware potentially contained can infect the recipient's computer or cell phone and damage both the data contained and the device itself, or exfiltrate the data.
If you want to report a specifically malicious phishing mail, please send it incl. header (!) to servicedesk (at) uni-graz.at so that we can perform an accurate analysis of the message. Without the metadata this is not possible.